
Scam in Dubai: Botim OTP Fraud Using Fake 200,000 AED Prize Targeting UAE Residents

Scam in Dubai is rising fast — especially dangerous attacks using Botim OTP fraud, fake 200,000 AED prize scams, and aggressive UAE mobile–number targeting. Every day, scammers impersonate trusted brands, tricking Dubai and UAE residents with fake “You won 200,000 AED” messages designed to steal accounts, reset passwords, and gain full control over your digital identity.
These attacks are not random. Scammers use VoIP apps like Botim, prize-based social engineering, and real UAE numbers to make the fraud look legitimate. Once they get your OTP, they can enter your accounts, change delivery locations, access payment wallets, and lock you out while they spend money in your name.
This guide exposes exactly how the Botim OTP scam in Dubai works, why the fake 200k AED prize trick is so effective, and how residents across the UAE can protect themselves from this new wave of digital fraud. All findings and recommendations here are published by CALLIT IT INFRASTRUCTURE, a cybersecurity-focused company in Dubai committed to protecting the public from rising digital threats.

How Scammers in Dubai Use Botim and Fake Al Ansari Calls
Scammers in Dubai and across the UAE are now using Botim voice calls to impersonate trusted financial brands like Al Ansari Exchange. They start by calling from what looks like a normal UAE number, showing a clean profile picture and even a fake company logo to appear legitimate. Their main tactic is the classic “You won 200,000 AED” script — a psychological trigger that pushes the victim to react before thinking.
Once the victim answers, the scammer claims that the “prize” cannot be released until the user confirms their identity. This is where the attack becomes dangerous. The scammer already entered the victim’s phone number into Botim, triggering a real OTP from Etisalat. When the victim receives this OTP, the scammer insists that it’s needed to “unlock the prize.” In reality, the OTP gives them full access to the victim’s Botim account and any linked services.
Inside Dubai, this method works extremely well because most residents trust local brands, trust UAE numbers, and don’t expect a fraudster to speak confidently about prizes, branches, and collection procedures. The entire scam is built on one goal:
👉
Get the victim to reveal the OTP
Once that happens, the scammer controls the account — not the victim.

Why UAE Residents Are Losing Money Through Their Mobile Numbers
Most UAE residents don’t realize how dangerously exposed their mobile number has become. Because so many apps in the UAE allow mobile-number–based payments, scammers only need one thing to drain your account: your OTP. Once they impersonate a trusted brand on Botim and trick you into sharing that code, they can immediately access your mobile-linked balance, top up wallets, add money, reset passwords, change delivery addresses, and lock you out of your own account — all without having your SIM card or device.
The problem is even worse because UAE residents commonly activate digital wallets, telecom payments, and in-app purchases using their Etisalat or Du phone number. That means your number isn’t just a contact detail… it has become a financial identity. When a scammer gains control of your app by registering it under your number, they gain the power to make purchases, verify transactions, and modify personal details using your identity. This is how people in Dubai and the wider UAE are losing money instantly — all from a simple OTP mistake.
CALLIT IT INFRASTRUCTURE is raising awareness about this because most victims do not understand that your phone number is now a financial key, and losing control of it — even for a few minutes — gives scammers access to everything behind it.

How Scammers Use Your UAE Number to Activate Apps on Their Devices
Scammers in Dubai are no longer relying on fake websites or complicated hacking methods. Instead, they install legitimate apps on their own phones — messaging apps, delivery apps, wallet apps, and even financial services — and then enter your UAE mobile number during registration. Because these apps allow manual number entry, the system sends the OTP to your device even though the scammer is the one registering the app. Once the victim receives the OTP, the scammer pretends it’s needed “to confirm identity” or “release a 200,000 AED prize,” tricking them into revealing the code.
The moment the OTP is shared, the scammer gains full access to the app under the victim’s number. From there, they can change personal details, modify recovery information, update delivery addresses, add payment methods, or even make purchases using mobile balance or in-app wallets. This method is extremely dangerous because it requires no SIM card cloning, no device access, and no technical skill — only a phone number and an OTP mistake. CALLIT IT INFRASTRUCTURE is raising awareness about this rising threat to protect Dubai and UAE residents from this fast and silent form of digital identity hijacking.

Why Emirates ID & Visa Scans Increase Digital Security Risks in the UAE
Across Dubai and the wider UAE, residents routinely hand over their Emirates ID, residence visa, or passport to building security teams for scanning. While this process is normal for access control, it creates a hidden digital threat: your most sensitive identity information is being handled by individuals you don't personally know, and you have no visibility into how the data is stored, whether it is copied, or where it may end up.
Many guards leave the job suddenly, change employers, or are replaced — but they may have already scanned hundreds of IDs that contain personal details such as full name, phone number, Emirates ID number, date of birth, visa information, and more. This becomes extremely dangerous when combined with OTP scams. Scammers use leaked ID details to impersonate institutions, sound credible, and pressure victims into sharing verification codes. CALLIT IT INFRASTRUCTURE is raising awareness because identity exposure + OTP fraud together create a high-risk environment for digital theft in Dubai.
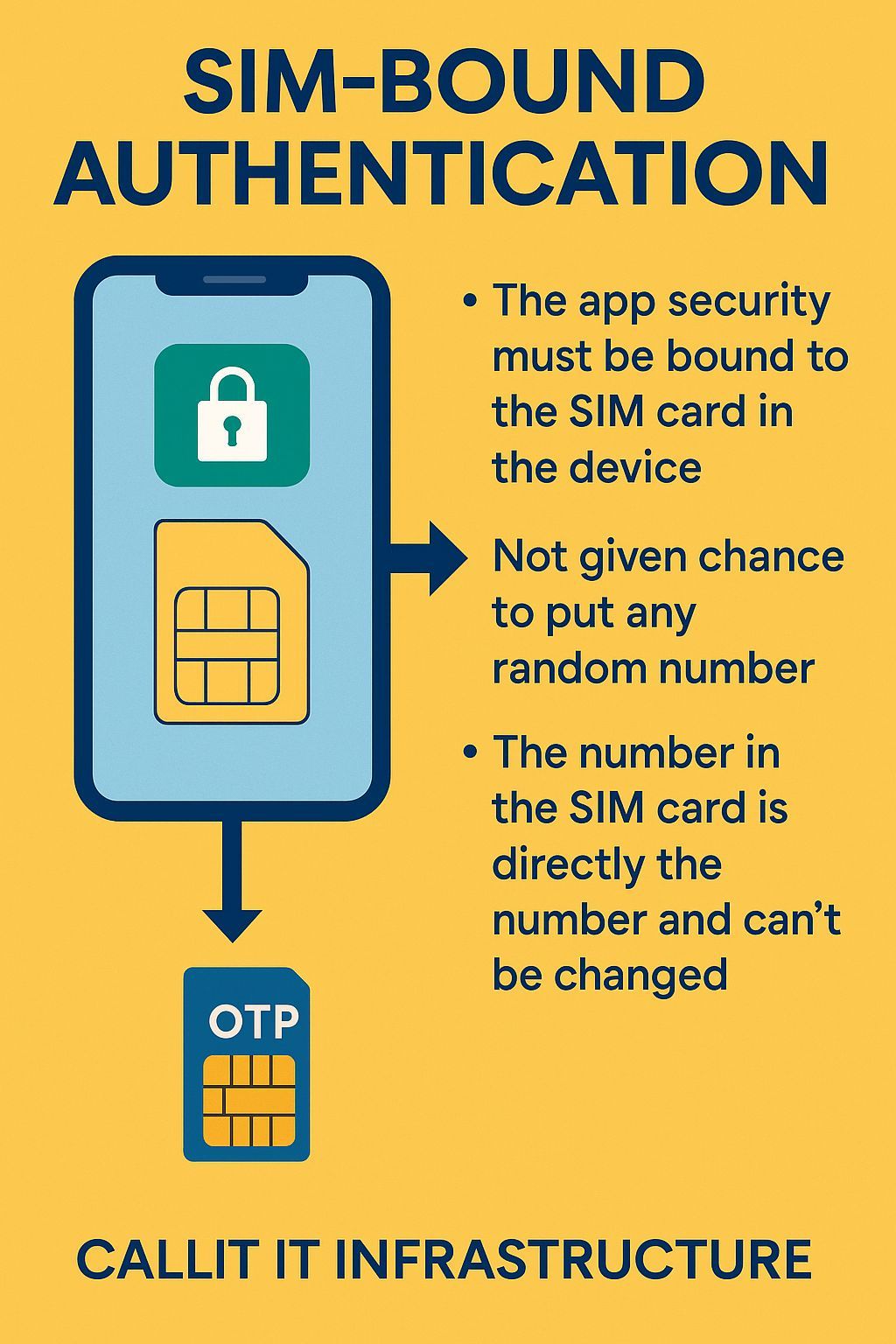
The Only Real Fix — SIM-Bound Authentication for UAE App Security
Most OTP scams in Dubai and the UAE succeed because apps allow users to manually type any mobile number during registration. This means scammers can install an app on their own device, enter a victim’s UAE number, and trigger an OTP without ever having the SIM card. As long as the victim reveals that OTP, the scammer instantly activates the app on their own phone and takes full control.
This entire weakness disappears the moment UAE apps adopt SIM-bound authentication. With this method, the app automatically reads the phone number directly from the SIM card inside the device, and the user cannot change it manually. If the SIM number doesn’t match the number attempting to register, the app blocks activation. This single improvement would stop 100% of remote OTP hijacking, fake prize calls, Botim impersonation, and mobile-number takeovers.
CALLIT IT INFRASTRUCTURE strongly recommends that UAE service providers adopt SIM-bound authentication to protect millions of residents from identity theft, unauthorized app access, and financial fraud. With a growing number of OTP-based attacks, this upgrade is no longer optional — it is essential for national digital safety.
This incident was reported to us by one of our customers, and CALLIT IT INFRASTRUCTURE is sharing this story to raise awareness and protect UAE residents from OTP scams, identity fraud, and unauthorized app activation attempts. For assistance or security-related guidance, you can contact us directly at +971 50 848 1467.
